
Managing Security for Web Apps, and APIs
Web Applications are preferred targets of threat actors. By targeting the application and API Layers, attackers can run malicious codes or make a ransomware attack.

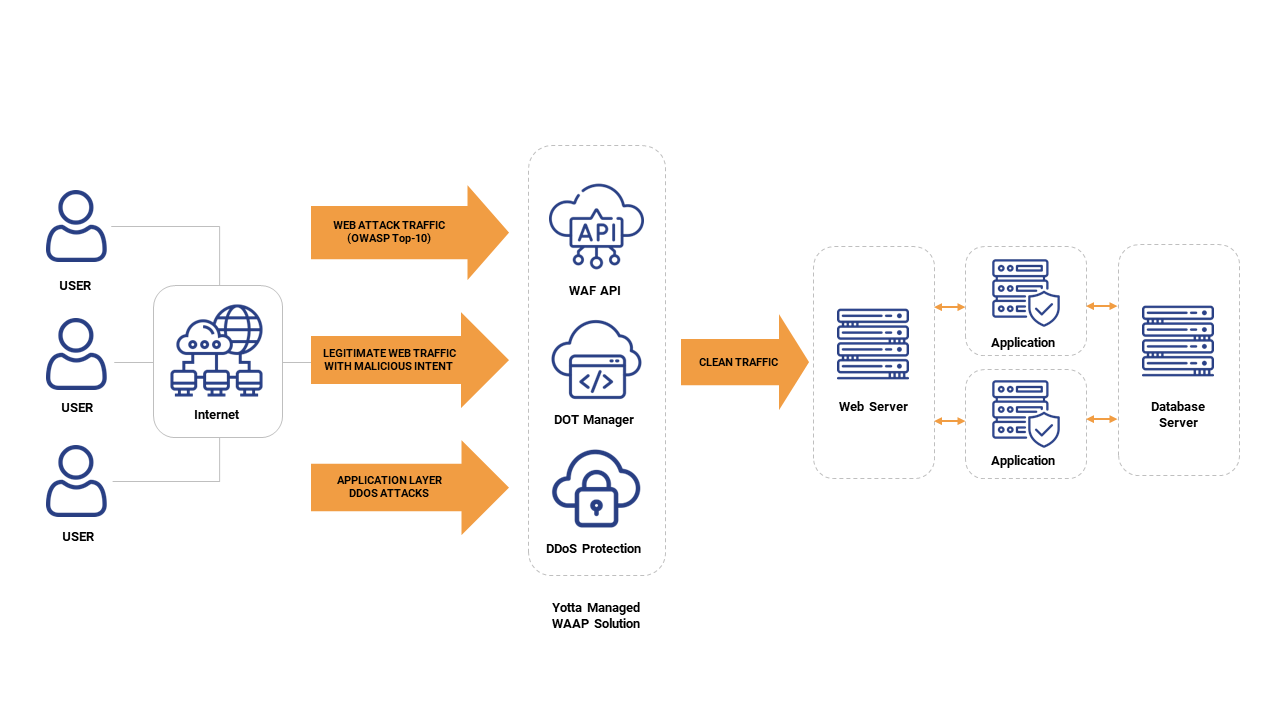
What is Managed WAAP?
Managed WAAP (Web Application and API Protection) is a comprehensive cybersecurity service that safeguards web applications and APIs from threats, offering continuous monitoring, threat detection, and response through a managed security solution.
API (Application Programming Interface) facilitates interaction between software components, enabling data exchange and functionality integration.

Why is Web Application and API Protection (WAAP) Important?
WAAP (Web Application and API Protection) is vital as it defends against cyber threats targeting web applications and APIs, safeguarding sensitive data, ensuring business continuity, maintaining customer trust, and complying with regulatory requirements.
Traditional network firewalls don’t work for HTTP, and these are inadequate. Application layer attacks are 1st preference for hackers, and with good reason.
They are relatively easy to execute, and the opportunities are virtually unlimited. Web applications are fertile ground for hackers, and they control the direct connection to the underlying databases.
Why Suraksha’s Managed WAAP Solution?
- Guaranteed performance-based SLA with 24×7 support
- Continuously protect against new and existing threats with machine-learning algorithms.
Shield Against OWASP Top 10 and Cloud Threats
Get comprehensive defense against OWASP Top 10 threats and cloud-based vulnerabilities, providing continuous monitoring, threat detection, and proactive mitigation to safeguard web applications and APIs.
Features
Still using WAF?
Enhance your protection.
Web applications and APIs are most vulnerable since they are accessible via the public Internet. Unfortunately, traditional security solutions are not effective enough to protect these applications. WAAP wins over traditional WAF due to the following reasons:

Ineffective Signature-based attack detection
WAAP offers continuous self-learning, which helps organizations keep ahead of a developing application security threat environment.

Port-based blocking being ineffective
Attacks against web applications and web APIs use the same web ports and protocols as users. Thus, filtering out malicious traffic becomes difficult.
HTTP traffic can be involved in the Web App
Level of security offered by a conventional intrusion detection and prevention system (IDS/IPS) is inadequate for isolating and protecting against threats to web applications.
Encrypted traffic inspection is necessary
Majority of web traffic today uses TLS encryption, which fails to detect malware and other malicious content. WAAP solutions can inspect TLS connections.
Integration with DevOps Workflow
WAAP seamlessly integrates with DevOps processes and tools, enabling automated security testing and deployment within CI/CD pipelines
Granular Protection
WAAP offers granular protection tailored specifically for web applications and APIs, allowing for more precise control over traffic and security policies



