
Strengthening Defences Through Vulnerability Assessment and Penetration Testing
Assess system weaknesses and simulate cyberattacks to fortify defenses, safeguarding against potential security breaches and ensuring robust protection of sensitive data and assets.

What is Vulnerability Assessment & Penetration Testing?
Vulnerability Assessment & Penetration Testing (VAPT) combines two critical security measures: a Vulnerability Assessment scans for weaknesses in your system, while Penetration Testing attempts to exploit those vulnerabilities, simulating real-world cyberattacks. This aids in identifying and rectifying security gaps before attackers can exploit them.

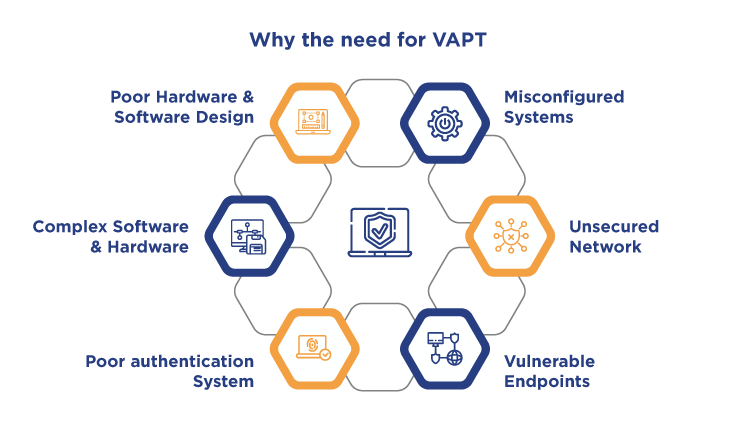
Why is Vulnerability Assessment & Penetration Testing Important?
Vulnerability Assessment & Penetration Testing is crucial because it exposes weaknesses in your defences before attackers do. By combining scans to find vulnerabilities and simulated attacks to exploit them, VAPT helps you fix security holes and prevent breaches, protecting your data and systems.

Why Suraksha’s VAPT
Suraksha’s Vulnerability Assessment & Penetration Testing service safeguards your organisation by providing visibility of security weaknesses and actionable guidance to mitigate them, ensuring compliance with industry standards. Our suite of automated scanning tools helps to assess potential vulnerabilities in your business network and identify potential attack points. Our penetration testing components can help identify weaknesses that might not be detectable with network or system scans.
Backed by a team of seasoned security professionals with industrial expertise, we’re your one-stop shop for comprehensive cybersecurity solutions. Our services not only identify vulnerabilities but also provide evidence of exploitation, enabling prompt remediation actions to assist in prompt remediation activities.
Reactive Response to Proactive Mitigation

Vulnerability Assessment
Vulnerability assessments utilise tools such as vulnerability scanners to detect threats and weaknesses within an organisation's IT infrastructure, exposing potential vulnerabilities or areas of risk.
These vulnerabilities may stem from various sources, including architecture or network design, difficult constructs in programming languages, Unsuccessful or misconfigured systems, systems connected to an unprotected network, Complicated hardware or software structure, weak password combinations, software errors, incorrect software settings, computer virus, or another type of malicious script injection or SQL injection. By identifying and addressing these vulnerabilities proactively, organisations can mitigate potential risks and enhance their overall security posture.

Penetration Testing
A penetration test, or pen test, is an authorised simulated attack performed on a computer system to evaluate its security. Penetration tests simulate a variety of attacks using the same tools, techniques, and processes that attackers might use. It is performed to prove the vulnerability and to understand the risk level in case such a vulnerability is exploited. Our penetration testing services offer capabilities to perform comprehensive manual penetration testing which surpasses all vulnerability scanning tools to provide in-depth results.

Application Security Testing (AST)
Application Security Testing (AST) involves assessing software applications for vulnerabilities and weaknesses that could be exploited by attackers. This includes both web and mobile applications. AST techniques include static analysis, dynamic analysis, and interactive testing. Static analysis examines application source code or binaries for vulnerabilities without executing the program. Dynamic analysis involves testing the application while it's running to identify vulnerabilities in real-time. Interactive testing combines static and dynamic techniques to provide comprehensive security assessments. AST helps organisations identify and mitigate security risks in their applications, reducing the likelihood of exploitation by attackers.

Red Team Assessment
It is a goal-based activity that requires a big-picture, holistic view of the organisation from an adversary perspective that attempts to exploit potential weaknesses using sophisticated attack techniques.
A security practise that has its roots in the military replicates full-spectrum cyberattacks, helps assess the efficiency of your cyber security against hostile actors and enables your defenders to test out and improve their detection and reaction skills in a safe setting.

Source Code Review
Assess identified business security risks implemented in the application’s development life cycle, security standards and guidelines. It is a manual and automated process that examines an application’s source code with a goal to identify any existing security flaws or vulnerabilities in an application code which can be in any programming language (java, .net, etc).
Scan the code of an application line-by-line with a code analyser deployed in a testing environment. The pentester manually checks them to eliminate false positives.

Firewall Configuration Review
A detailed review of your firewall configuration is performed to look for any deviations from security best practices that could potentially leave your system vulnerable to attack.
The deficiencies may include gaps in rules and their granularity, weak access controls, deficient managed procedures, lack of security patch updates and so on.
These devices are typically one of the main security tools you employ to safeguard your network and, consequently, the sensitive data it holds.

Network & Infrastructure Assessment
Network and infrastructure assessment involves evaluating systems and software implemented to safeguard the underlying networking infrastructure against unauthorised access, data deletion, or modification.
Industry Standard Processes for VAPT
A structured, scientific, and mature approach is followed for Vulnerability Assessment and Penetration Testing (VAPT), whether it's for network, mobile, or website penetration testing. This process begins with reconnaissance and enumeration on the defined target, followed by scanning and identification of security vulnerabilities and misconfigurations across all assets. Subsequently, penetration testing is conducted through controlled attacks to exploit encountered vulnerabilities and misconfigurations. Finally, a risk analysis report is generated to understand gaps, explain the impact, and suggest rectification procedures.
Use Cases

