
Monitor, Detect, And Prevent Unauthorised Access
Tighten security around critical systems. Privileged Access Management (PAM) controls access and activity of privileged users, safeguarding your most valuable data.

What is Privileged Access Management (PAM)?
PAM is a cybersecurity approach that focuses on managing and securing privileged accounts, credentials, and access rights to protect critical systems and sensitive data from misuse or unauthorized access.
PAM acts like a digital vault for high-level accounts. It controls who can access critical systems and monitors their activity, protecting your most sensitive data.

Why is Privileged Access Management Important?
Organisations need protection against accidental or purposeful misuse of privileged access. PAM helps streamline the authorisation and monitoring of privileged users to ensure this protection. The best way to prevent attacks is by controlling and monitoring privileged user access to your most critical data and systems.
Why Suraksha’s Privileged Access Management (PAM)
- Quick deployment with setup availability on Day 0
- Credential management, session monitoring, and controlling to help customers with regular Audits and Compliance
- Ensure regular upgrades without managing it or doing manual upgrades
- Experienced expertise with 24×7 availability
How PAM Works
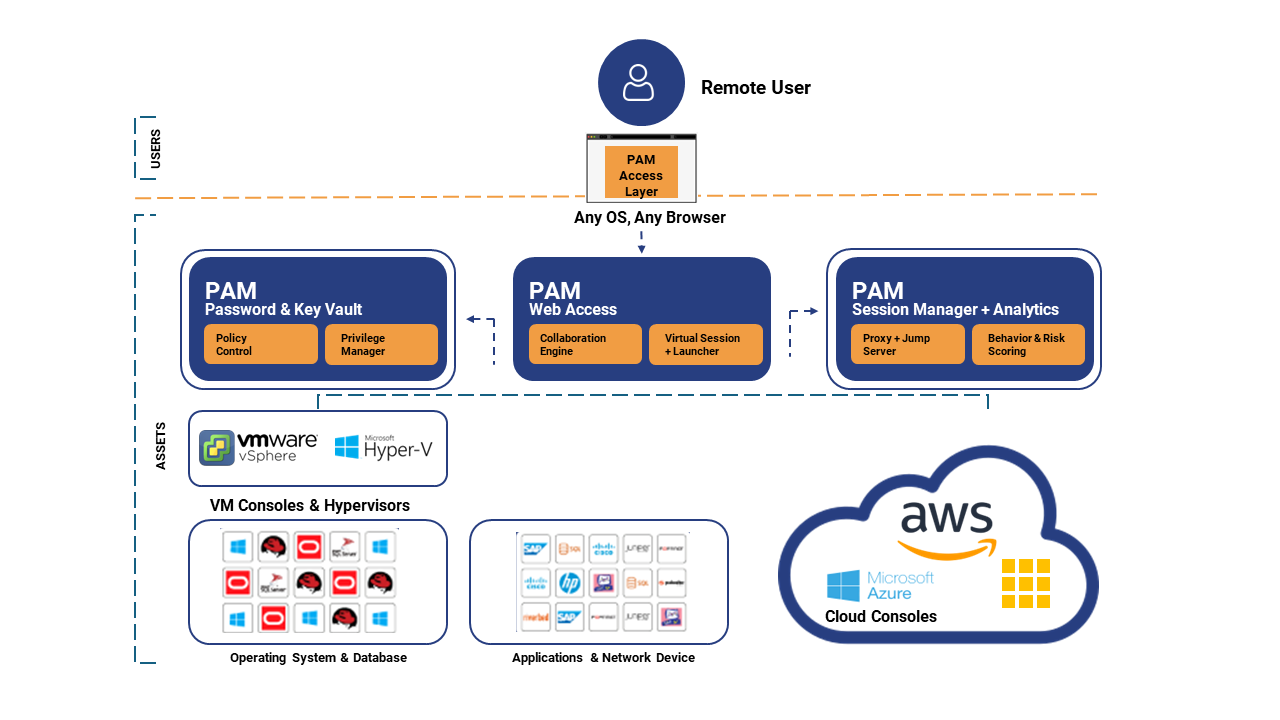
Secure Access with Password Management & Session Management Capabilities
Deploy in a matter of minutes and integrate workloads from different clouds. Ensured password security. A single platform to empower all teams, from vendors to app users. Enable single sign-on & secure access with controlled sessions and password management.

Operational Efficiency
Drive Operational Efficiency through Automation, Resource Optimization, Central management, Simplifying audit and reporting

Security
Secure your data from Targeted Attacks, Insider Threats, Passwords Leakage Issues and Maintain internal control

Compliances
Ensure various compliances like RBI Compliances, IRDA & SEBI Compliance, ISO 27001, PCI DSS, Co-Op Bank Guidelines, etc
With unified privileged, remote access, and endpoint privileged management, discover unlimited possibilities.
Time Saving
High speed of deployment of PAM saves time, ensuring protection from day one.
Increased automation
With dynamic groups, policy with reconciling passwords & keys, access can be automated without human intervention.
Automatic updates of Applications/systems
Perform system updates or changes automatically without hampering productivity.
Better predictability of costs
Significantly less investment because of Opex Model. No additional budget to be allocated for infrastructure, maintenance, updates, resources, etc.
Robustness and Scalability
Leverage deep AD integration capabilities to work with assets & users managed via Active Directory.
Flexibility of deployment
Easier Adaption because of operational efficiency and flexible deployment.

